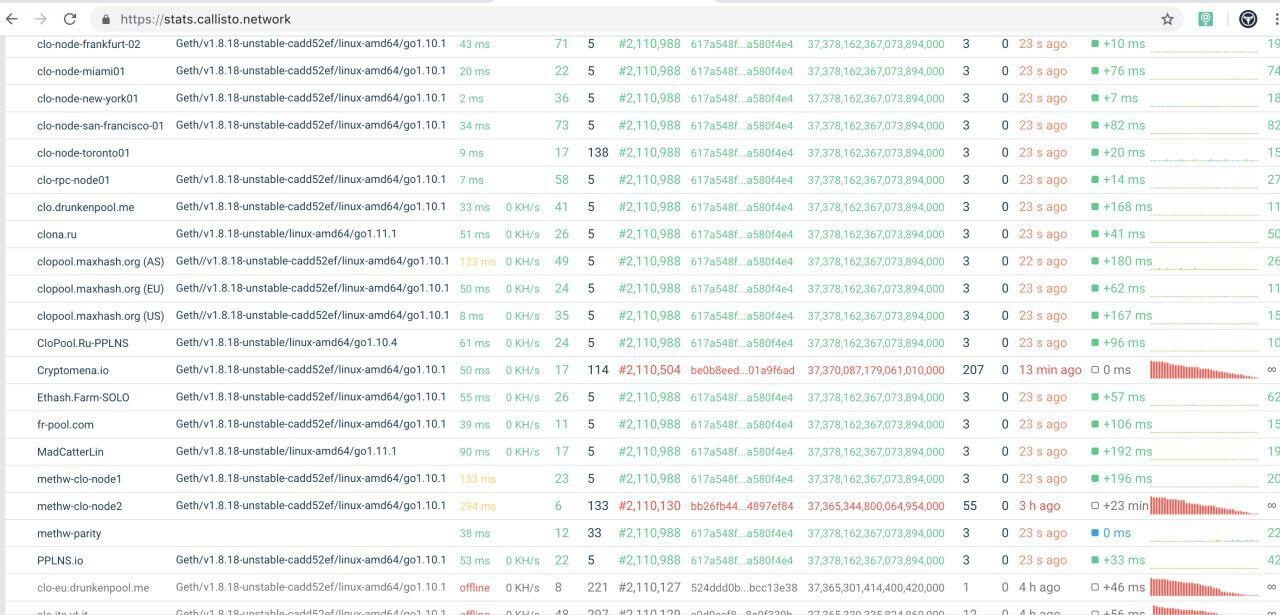
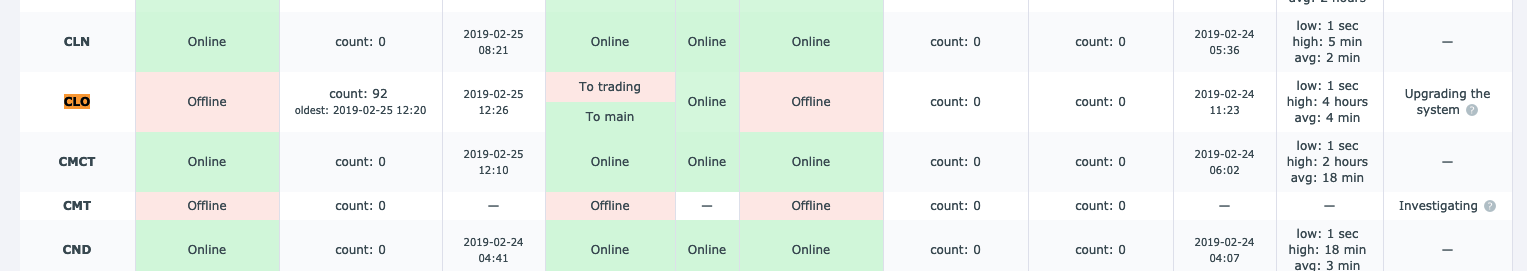
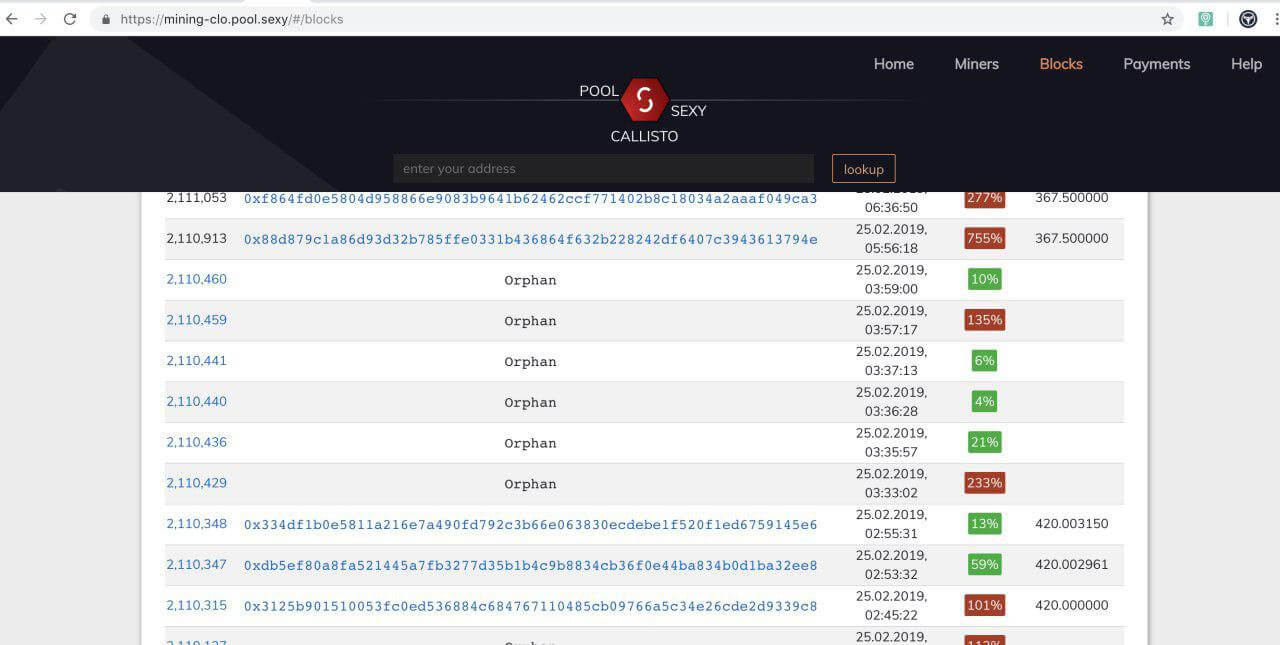
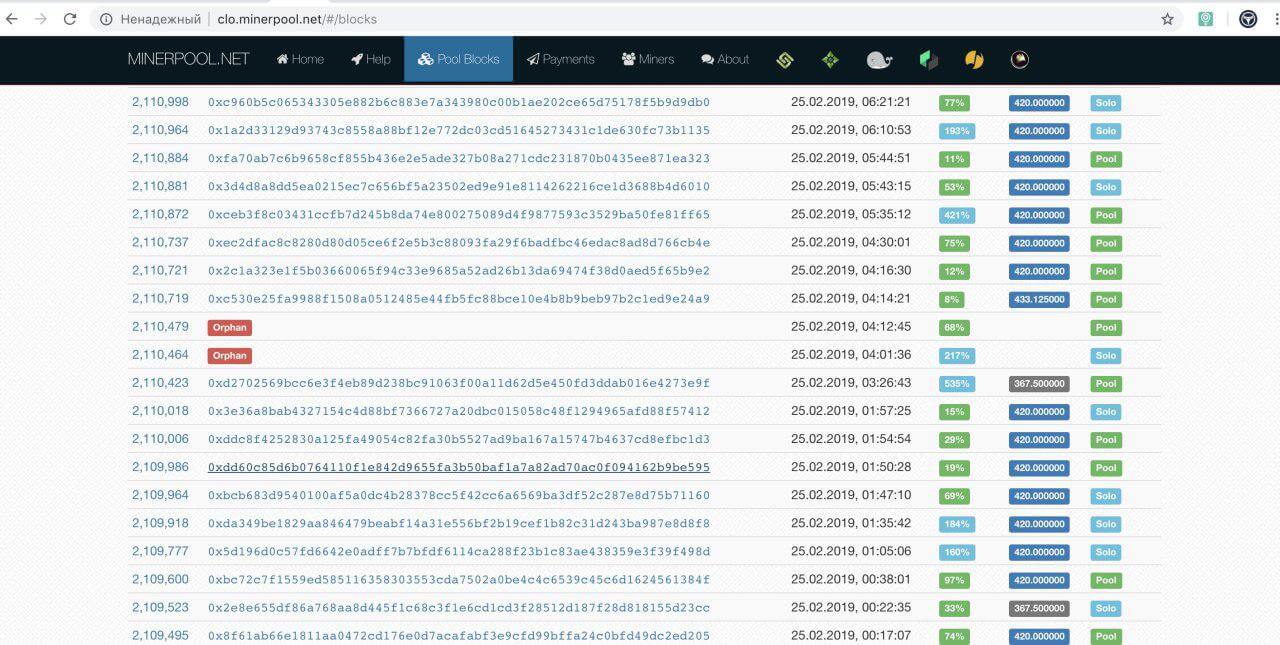
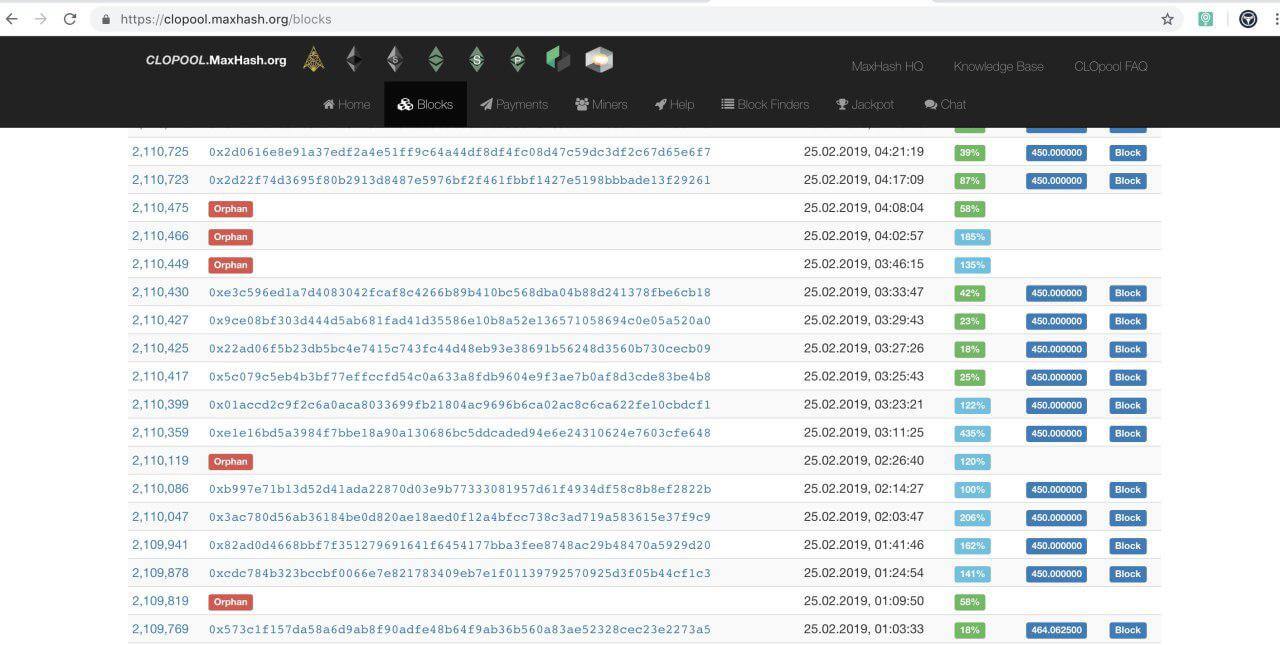
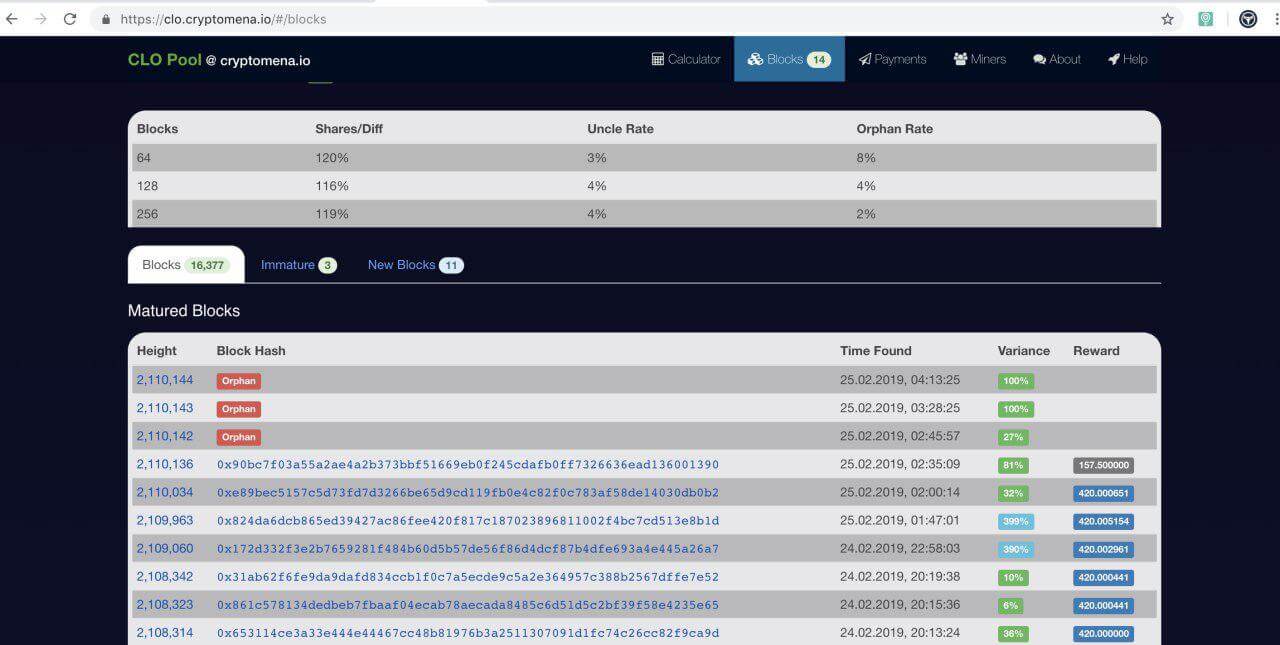
Some of the Callisto nodes including the nodes of the pools have gone to the wrong chain.
Contents
Our Investigation
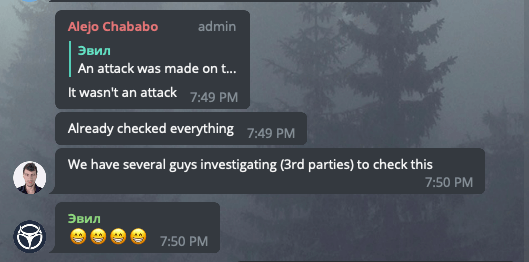
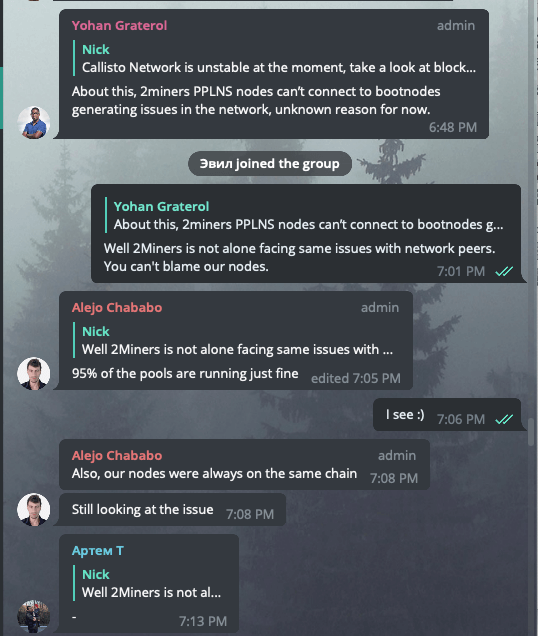
We are almost sure the bootnodes have gone to the different chains as well. However, CLO developers say everything was fine. When we discovered the problem, we’ve immediately informed the Callisto community in Telegram. As a result, our lead blockchain engineer has been banned there.
The Callisto representative answer was that everything works fine with Callisto. They said the problem was on our side only. 95% of the pools as they told were operating fine.
In a meantime, major exchanges immediately halted CLO withdrawals.
Usually, exchanges look after coins networks better than the coin developers itself, since any unstable chain it’s potentially money loss for exchange.
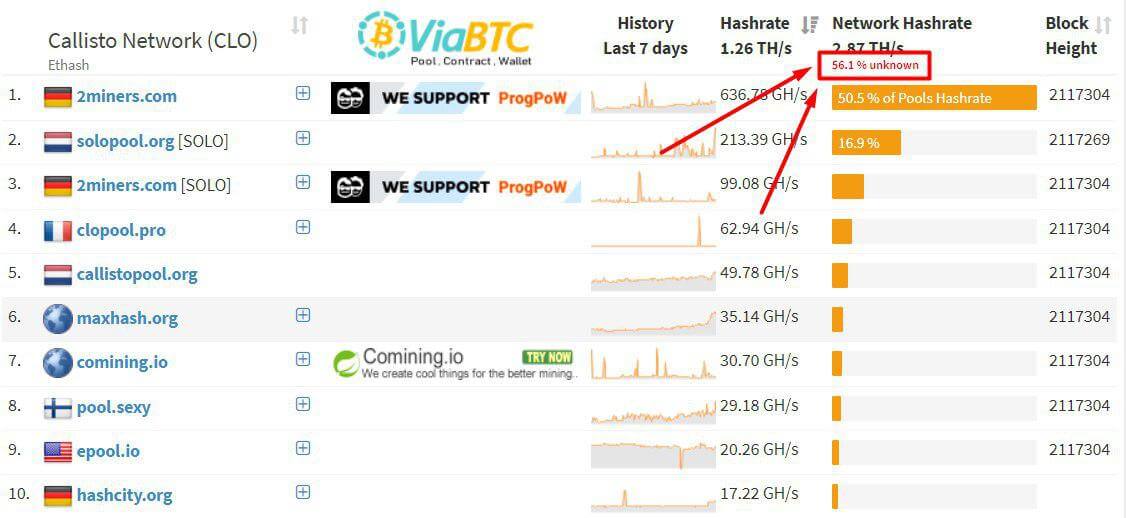
CLO Mining Pools Under Attack
We’ve made an investigation and found out that this was the attacker’s address 0x43df132c06dad50d94462e8b86988ba1c78dfb24. There were multiple pools which received the orphan blocks caused by this attack.
Obviously, the Callisto representatives were wrong. There was a conventional and well known 51% attack. This kind of attacks has been performed on many Ethash coins recently including MOAC, ETC, and others.
2Miners Mining Pool During the Chain Split
Unfortunately, 2Miners CLO PPLNS pool has gone to the wrong chain after the chain split. This caused a considerable amount of CLO blocks to be wrongly confirmed. The payouts have been stopped for a short period. 167 000 CLO(~$800) in total has been confirmed by mistake. We’ve provided all the information to the Callisto developers. It took some time for them to make a decision and the final answer was “We take responsibility but we will not refund in all cases.” In the end, Callisto Network Team agreed they had a problem, but they don’t care about miners losses.
They said they were auditing and testing PirlGuard and Komodo dPoW to prevent the 51% attacks for about a month. However, seems the implementation is delayed for an unknown period of time, and not even mentioned at the roadmap. The only one advice, 12 hours later after the attack, was to increase the block confirmation time to 300 new blocks. This means each new block would be confirmed in about 75 minutes.
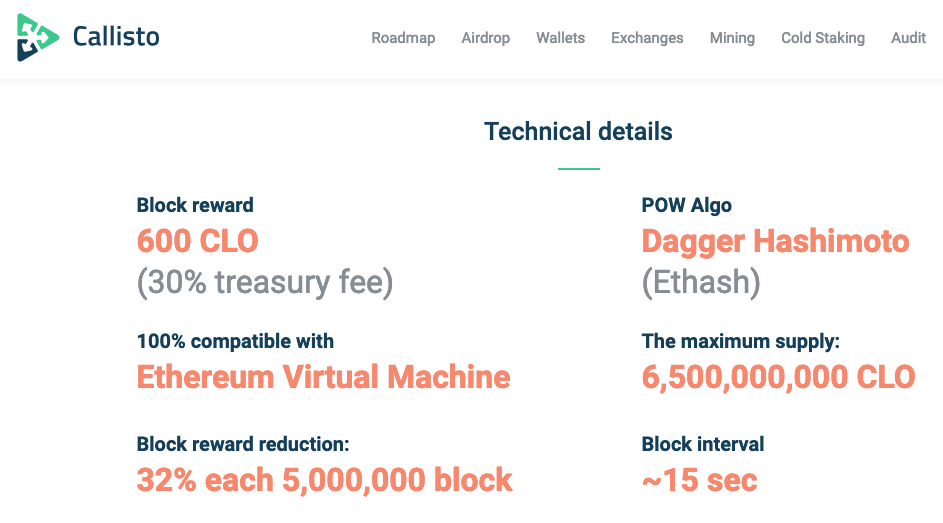
It sounds ridiculous that the third largest Ethash coin backed by a dev-fee model(each mined block contains 30% treasury fee) failing to properly and timely take appropriate actions against 51% attacks.
Another great achievement of Callisto Team was that they were actively shushing this problem and blaming us for talking about it publicly. Since 2Miners is 100% transparent pool it’s unacceptable for us.
Our brand reputation is worth much more than $800, so we’ve bought 167K CLO on the exchange and performed the pending payments to our miners today.
Callisto Network Issues May Happen Again
At the moment 2Miners mining pools (both PPLNS and SOLO) are operating correctly, the network seems stable working, and the payouts have proceeded as they should.
We also improved our proprietary blockchain monitoring system to prevent payouts when the network in a chain split state.
Unfortunately, there is no guarantee that the attack will not happen again unless the Callisto developers do something to prevent it. What is sadder they don’t care about the miners. They want their coin to be traded on different exchanges and wait for the price to reach the moon, but they do nothing to support and protect the miners.
What Could Be Done to Prevent 51% Attacks?
There is few ready to go solutions on the market right now: PirlGuard and Komodo Platform’s delayed Proof of Work (dPoW) are most common for Ethash coins. Also it worth to mention here collection of bash scripts to collect and analyze blockchain client metrics, providing basic alerting mechanisms for unusual events and situations developed by ETCLabs.
Update. The Attacks Continue
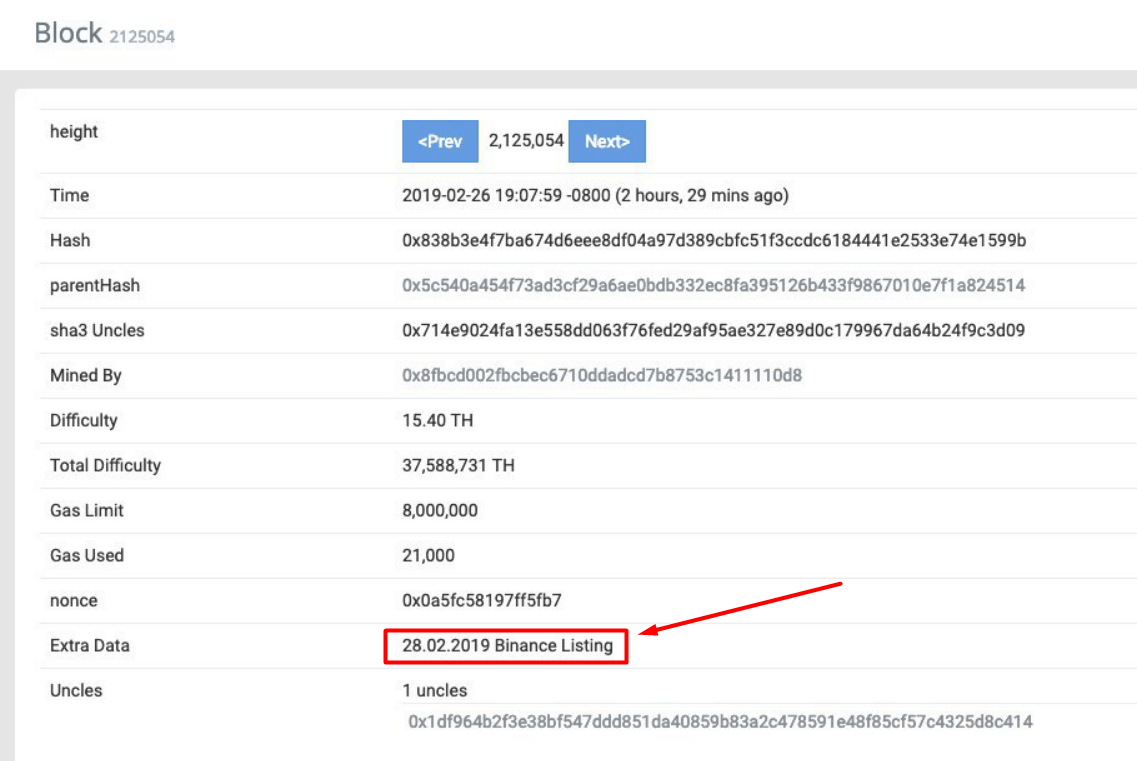
Callisto Network (CLO) has been attacked again. We’ve stopped the payouts for a short period of time while the network was unstable. This time the attacker was playing with Extra Data in the blocks. Sometimes the attacker pretended to be a 2Miners pool. The other blocks he wrote “28.02.2019 Binance Listing” in Extra Data field.
Callisto Network Emergency Hardfork
CLO developers team has called the emergency hard fork on block 2 160 000 (approx. March 5). Please mine Callisto on your own risk until this date. If the attacks continue there is a chance of receiving Orphan blocks -> less daily rewards. What is an Orphan block?